The Microsoft 365 Software-as-a-Service solution is wildly popular and is continuing to gain momentum among businesses and users alike. It offers a wide range of great cloud-driven features that allow end-users to work and collaborate much more efficiently with modern tools.
However, despite the benefits and capabilities that are afforded by cloud environments like Microsoft 365, cybersecurity continues to be a concern. What can end-users do to help minimize cybersecurity risks to their data stored in Microsoft 365? Let’s take a look at cybersecurity tips for Microsoft 365 users that can help minimize threats to their data.
Cybersecurity Tips for Microsoft 365 Users
When we think about cybersecurity tips for end-users using Microsoft 365, it involves a good mix of not only technical solutions but also, end-user security-conscious behaviors. The actions of end users can be just as critical as the technology aspects of a balanced cybersecurity plan for cloud data.
Let’s take a look at the following cybersecurity tips for Microsoft 365 users:
- Setup multi-factor authentication
- Stay alert to phishing emails
- Share information from the cloud with caution
- Do not install risky third-party applications
- Maintain a security mindset
We will examine each one of these cybersecurity tips and why each is extremely important to help secure your Microsoft 365 environment.
1. Setup multi-factor authentication
One of the weakest links in the security for Microsoft 365 users is passwords. Despite password policies and other technologies that can help with making passwords more secure by enforcing certain complexities, they are still a weak link.
One of the easiest cybersecurity tips for Microsoft 365 users involves turning on multi-factor authentication (MFA). Often this is commonly implemented in the form of two-factor authentication. With two-factor authentication, logins require that you enter something “you know – the password” along with proving your identity with “something you have – your phone or other devices”.
When you log in with the correct password to Microsoft 365 with multi-factor authentication turned on, the authentication is still not successful until you validate that you are the authorized user who that password belongs to. This is usually done by verifying a One-Time Password that is either texted to a smartphone or via an automated software solution such as with Microsoft Authenticator. With the Microsoft Authenticator, you can simply tap a button to approve the login request that is pushed to your phone.
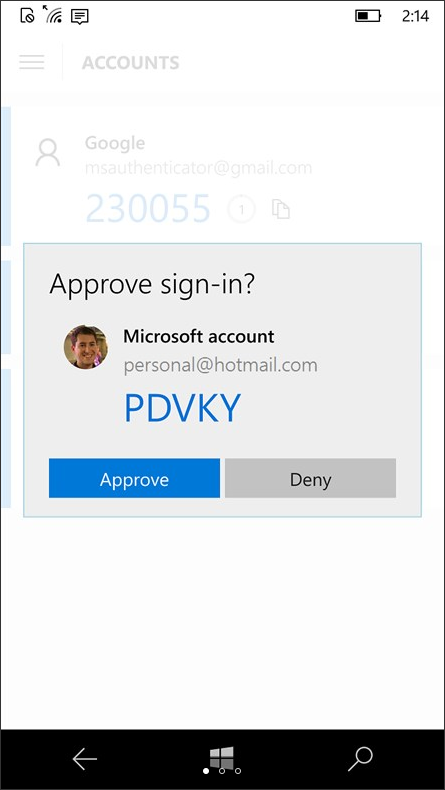
Using Microsoft Authenticator provides easy two-factor authentication
If an attacker is not in possession of both the password and the multi-factor device, the login attempt will be rejected. Enabling multi-factor authentication helps to greatly improve the overall security for a Microsoft 365 user.
2. Stay alert to phishing emails
Despite being a rather archaic tactic used by attackers to compromise environments, phishing is still very effective and has evolved in its sophistication. This is especially true in the realm of email. Phishing emails account for a large number of ransomware and other malware infections that affect the organization’s end users. It is once again an attack method that has come back into “style” as one of the most common tools that hackers employ.
Phishing emails are generally very effective since they masquerade as legitimate communications from respected organizations you may be familiar with or even from individuals you know personally. When this is the case, you may quickly let our guard down and readily submit the information requested, install applications, or grant requested permissions in the Microsoft 365 cloud environment. The “applications” that phishing emails may link to often contain a malicious ransomware payload.
A great cybersecurity tip for Microsoft 365 users is to watch for the tell-tale signs that characterize a phishing email. These may include the following:
- The “reply-to” address does not match the sender’s address
- There are obvious misspellings in the email
- The logos and other images contained in the email may be very low quality and have the appearance of being copied and pasted from a website
- Even though the email may appear to be from someone familiar, it is asking you to do things you wouldn’t normally be asked to do (email back sensitive information, paste in payment details, click links, or install software).
By being alert to certain characteristics of phishing communications, it can help to avoid falling victim to a phishing scam which may expose your organization to ransomware or data leak.
Share information from the cloud with caution
One of the tremendous advantages of cloud environments like Microsoft 365 is the ease in which information can be shared with other users, both within the M365 organization and even external users. However, this easy ability to share information can also be the “Achilles heel” from a cybersecurity standpoint.
Sharing the wrong or sensitive information either accidentally or intentionally can lead to dire consequences for your organization. Data leak disasters often start with seemingly insignificant actions of sharing a simple file, folder or sending an email outside your organization.
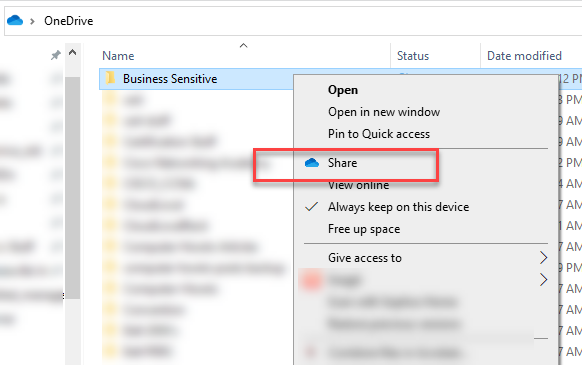
Cloud tools make it easy to share data that may lead to data leak
A data leak can lead to tremendous fiscal consequences for businesses whose end-users leak data. According to IBM’s 2019 Cost of a Data Breach Report, the consequences of data leak are staggering.
Below are highlights of the report:
- The global average cost of a data breach – $3.92 million
- Cost per record – $150
- Time to identify and contain a breach – 279 days
- Highest country average cost – U.S., $8.19 million
- Highest industry average – Healthcare, $6.45 million
It is imperative that Microsoft 365 end users are careful with data sharing or transmission outside of the sanctioned boundaries defined by the business. Not only can data be leaked accidentally, but attackers are also quick to seize the opportunity via phishing as mentioned earlier, ransomware, or other means to gain access to data that can be leaked for profit or other gains.
New forms of ransomware are “sharing” cloud data for you. Attackers are using new tactics such as the threat of data leak for those organizations that decide not to pay the ransom to get their data back. This makes it even more important for Microsoft 365 users to scrutinize emails, data sharing requests, third-party applications that are unknown, and other means they can succumb to leaking data.
Ultimately, a great cybersecurity tip for Microsoft 365 users involves using extreme caution when sharing cloud data with others. Make doubly sure you are sharing information with who you think you are sharing with. Understand the risks of inadvertently exposing your organization to a breach of sensitive data.
Do not install risky third-party applications
One of the great things about cloud Software-as-a-Service (SaaS) environments like Microsoft 365 is the huge selection of third-party applications. These applications available to Microsoft 365 users allows extending the native capabilities found in Microsoft 365 with additional features and functionality.
Microsoft 365 app source provides access to thousands of apps for M365
With the tremendous advantages that come from easily adding features and capabilities to Microsoft 365 by means of installing third-party apps, this can lead to cybersecurity risks as well. Attackers are well aware of how most users blindly install third-party applications, granting the permissions requested without scrutiny.
They can use this to easily compromise an entire Microsoft 365 organization. By granting permissions to a malicious third-party application, a Microsoft 365 user can expose their data as well as the data of the entire organization to the dangers of ransomware as well as a data leak.
Kevin Mitnick demonstrated how easily a malicious third-party application when granted permissions requested, could easily encrypt an entire user’s mailbox in real-time. It demonstrates the need to be vigilant when installing any third-party application. Make sure to only install reputable applications. Never install an application that you are encouraged to install by means of an email you receive.
Always scrutinize the permissions that are requested by an application. Never blindly accept all the permissions that an application requests during an installation. Giving proper attention to permissions requested may very well help to prevent a malicious application masquerading as a legitimate app from having the permissions it needs to completely compromise the environment.
Maintain a security mindset
One of the most important cybersecurity tips for Microsoft 365 users that is an underlying theme throughout all the other cybersecurity tips described already is to maintain a security mindset. For a user, this involves a sense of security awareness and vigilance to potential risks both on-premises and using cloud SaaS environments like Microsoft 365.
Security awareness training can help you to understand what certain attacks may look like. It can help to identify:
- Phishing attacks
- Malicious and risky applications
- Email-based attacks
It also helps to have better overall security hygiene and understand what steps to take to be more careful when navigating across the web, using cloud resources, and attain better familiarity with corporate policies. It can also help train what steps to take if you suspect you have fallen victim to a cybersecurity attack. Keeping yourself, your data, and your organization’s data secure in Microsoft 365 is a matter of using good common sense and keeping security at the forefront of everything you do.
There is another extremely important aspect of cybersecurity – backups. How can organizations properly protect the business-critical data of Microsoft 365 users?
Backup Microsoft 365 Data
Having effective backups of your data is one of the most basic components of an effective cybersecurity strategy. At the end of the day, if you suffer a ransomware attack or other cybersecurity disaster that leaves your data unreadable, restoring from a backup is the only option.
Microsoft 365 includes built-in versioning of OneDrive for Business and SharePoint Online that allows restoring your files back to a previous version within the past 30 days. While the built-in capability provided in Microsoft 365 is a good start, it falls short for providing the protection needed for most organizations. How can end-user data be effectively protected?
SpinOne is a solution including SpinBackup for Microsoft 365 cloud-to-cloud data protection that provides enterprise-grade backups of your Microsoft 365 environment. It allows your business to properly protect business-critical data that exists in OneDrive for Business, Exchange Online, SharePoint Online, Contacts, and Calendar. SpinBackup includes features and capabilities that allow you to meet Office 365 backup best practices.
- Automatic backups of your data – 1-3x daily
- Ability to store backups in Amazon AWS, Microsoft Azure, and Google GCP storage
- 100% accurate recoverability for your data
- Ability in one click to migrate user data from one account to another
- Search and find data in backups easily
- Perform granular or in-bulk restores
- Encrypted backups both in-flight and at-rest
- Single pane-of-glass interface for backups
- Part of the SpinOne cybersecurity features to protect against ransomware
SpinOne uses the powerful features provided by SpinBackup to provide industry-leading ransomware protection for Microsoft 365. SpinOne provides AI-driven, fully-automated responses to a ransomware attack that affects your environment.
To learn more about the features provided by SpinOne, including SpinBackup and cloud ransomware protection, take a closer look here.